Lead4pass SCS-C02 dumps 2025 have been updated! Helps you prepare for the AWS Certified Security – Professional (SCS-C02) certification exam!
Overview of leads4pass SCS-C02 dumps:
Leads4Pass SCS-C02 dumps provide complete SCS-C02 exam preparation materials and are guaranteed to be actually useful!
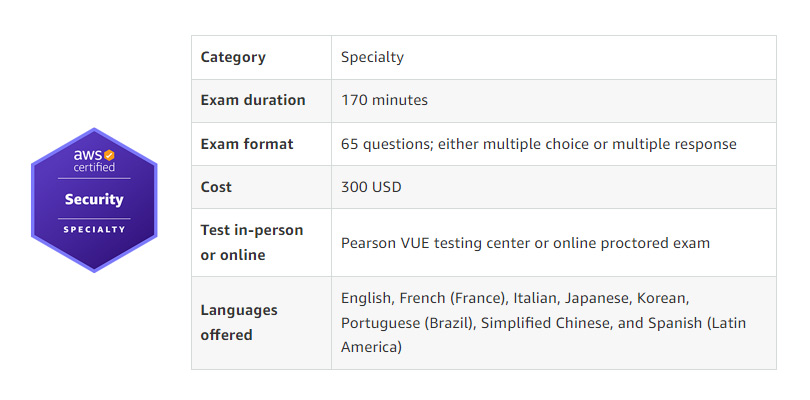
| Exam name: | AWS Certified Security – Specialty |
| Exam code: | SCS-C02 |
| Total Questions: | 816 Q&A |
| Practice method: | PDF, VCE, PDF+VCE |
| Serve: | 24/7(liveChat, Contact) |
| Member time: | 365 days Free Update |
| More: | https://www.leads4pass.com/scs-c02.html (816 Q&A) |
AWS Certified Security – Specialty(scs-c02) Exam Overview: https://aws.amazon.com/certification/certified-security-specialty/ (Specific details of the SCS-C02 exam, including exam time, registration method, price…)
Exam preparation:
Understand the SCS-C02 exam and exam question types
The AWS Certified Security – Specialty (SCS-C02) exam is intended for individuals who
perform a security role. The exam validates a candidate’s ability to effectively
demonstrate knowledge about securing AWS products and services.
The exam also validates whether a candidate has the following:
- An understanding of specialized data classifications and AWS data protection
mechanisms - An understanding of data-encryption methods and AWS mechanisms to
implement them - An understanding of secure internet protocols and AWS mechanisms to
implement them - A working knowledge of AWS security services and features of services to
provide a secure production environment - Competency from 2 or more years of production deployment experience in
using AWS security services and features - The ability to make tradeoff decisions regarding cost, security, and deployment
complexity to meet a set of application requirements - An understanding of security operations and risks
The target candidate should have the equivalent of 3–5 years of experience in
designing and implementing security solutions. Additionally, the target candidate
should have a minimum of 2 years of hands-on experience in securing AWS
workloads.
Response types
There are two types of questions on the exam:
- Multiple choice: Has one correct response and three incorrect responses
(distractors) - Multiple responses: Has two or more correct responses out of five or more
response options
Select one or more responses that best complete the statement or answer the
question. Distractors, or incorrect answers, are response options that a candidate with
incomplete knowledge or skill might choose. Distractors are generally plausible
responses that match the content area.
Unanswered questions are scored as incorrect; there is no penalty for guessing. The
exam includes 50 questions that affect your score. Get More>>
Understand the exam topics
Course Objectives:
- Identify the security benefits and responsibilities when using the AWS Cloud
- Describe the access control and management features of AWS
- Understand the different data encryption methods to secure sensitive data
- Describe how to secure network access to your AWS resources
- Determine which AWS services can be used for security logging and monitoring
Course Outline:
- Introduction to AWS Security Fundamentals
- Security of the Cloud
- AWS Global Infrastructure
- Data Center Security
- Compliance and Governance
- DDoS Mitigation
- Entry points on AWS
- Identity and Access Management
- Detective Controls
- Infrastructure Protection
- Data Protection
- Incident Response
- Well-Architected Tool Overview
- End of Course Assessment
Prepare and evaluate your preparation for the SCS-C02 exam
Practice the 2025 New AWS Certified Security – Specialty (SCS-C02) dumps exam questions online for free
| From | Number of exam questions | Free Download | Related exams |
| leads4pass | 15 | Leads4Pass SCS-C02 PDF | AWS Certified Specialty |
New Question 1:
An Amazon EC2 Auto Scaling group launches Amazon Linux EC2 instances and installs the Amazon CloudWatch agent to publish logs to Amazon CloudWatch Logs. The EC2 instances launch with an IAM role that has an IAM policy attached. The policy provides access to publish custom metrics to CloudWatch. The EC2 instances run in a private subnet inside a VPC. The VPC provides ^ccess to the internet for private subnets through a NAT gateway.
A security engineer notices that no logs are being published to CloudWatch Logs for the EC2 instances that the Auto Scaling group launches. The security engineer validates that the CloudWatch Logs agent is running and is configured properly on the EC2 instances. In addition, the security engineer validates that network communications are working properly to AWS services.
What can the security engineer do to ensure that the logs are published to CloudWatch Logs?
A. Configure the IAM policy in use by the IAM role to have access to the required cloudwatch: API actions that will publish logs
B. Adjust the Amazon EC2 Auto Scaling service-linked role to have permissions to write to CloudWatch Logs.
C. Configure the IAM policy in use by the IAM role to have access to the required AWS logs: API actions that willpublish logs.
D. Add an interface VPC endpoint to provide a route to CloudWatch Logs.
Correct Answer: A
New Question 2:
Your developer is using the KMS service and an assigned key in their Java program. They get the below error when running the code arn:IAM:iam::113745388712:user/UserB is not authorized to perform: kms:DescribeKey Which of the following could help resolve the issue?
A. Ensure that UserB is given the right IAM role to access the key
B. Ensure that UserB is given the right permissions in the IAM policy
C. Ensure that UserB is given the right permissions in the Key policy
D. Ensure that UserB is given the right permissions in the Bucket policy
Correct Answer: C
You need to ensure that UserB is given access via the Key policy for the Key
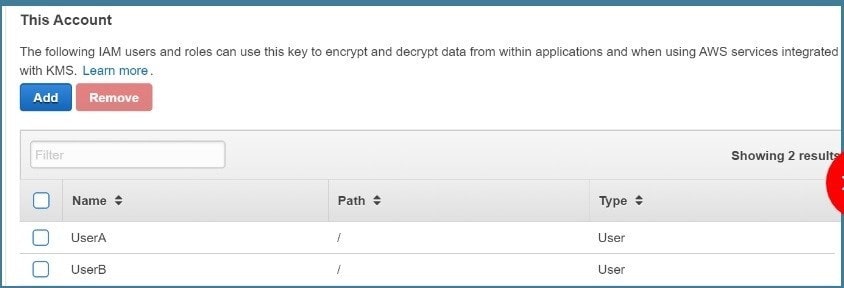
Option is invalid because you don\’t assign roles to IAM users For more information on Key policies please visit the below Link: https://docs.IAM.amazon.com/kms/latest/developerguide/key-poli The correct answer is: Ensure that UserB is given the right permissions in the Key policy
New Question 3:
A company runs workloads in the us-east-1 Region. The company has never deployed resources to other AWS Regions and does not have any multi-Region resources.
The company needs to replicate its workloads and infrastructure to the us-west-1 Region.
A security engineer must implement a solution that uses AWS Secrets Manager to store secrets in both Regions. The solution must use AWS Key Management Service (AWS KMS) to encrypt the secrets. The solution must minimize latency and must be able to work if only one Region is available.
The security engineer uses Secrets Manager to create the secrets in us-east-1.
What should the security engineer do next to meet the requirements?
A. Encrypt the secrets in us-east-1 by using an AWS managed KMS key. Replicate the secrets to us-west-1. Encrypt the secrets in us-west-1 by using a new AWS managed KMS key in us-west-1.
B. Encrypt the secrets in us-east-1 by using an AWS managed KMS key. Configure resources in us-west-1 to call the Secrets Manager endpoint in us-east-1.
C. Encrypt the secrets in us-east-1 by using a customer managed KMS key. Configure resources in us-west-1 to call the Secrets Manager endpoint in us-east-1.
D. Encrypt the secrets in us-east-1 by using a customer managed KMS key. Replicate the secrets to us-west-1. Encrypt the secrets in us-west-1 by using the customer managed KMS key from us-east-1.
Correct Answer: D
To ensure minimal latency and regional availability of secrets, encrypting secrets in us- east-1 with a customer-managed KMS key and then replicating them to us-west-1 for encryption with the same key is the optimal approach. This method leverages customer- managed KMS keys for enhanced control and ensures that secrets are available in both regions, adhering to disaster recovery principles and minimizing latency by using regional endpoints.
New Question 4:
DDoS attacks that happen at the application layer commonly target web applications with lower volumes of traffic compared to infrastructure attacks. To mitigate these types of attacks, you should probably want to include a WAF (Web Application Firewall) as part of your infrastructure. To inspect all HTTP requests, WAFs sit in-line with your application traffic. Unfortunately, this creates a scenario where WAFs can become a point of failure or bottleneck. To mitigate this problem, you need the ability to run multiple WAFs on demand during traffic spikes. This type of scaling for WAF is done via a “WAF sandwich.” Which of the following statements best describes what a “WAF sandwich” is? Choose the correct answer from the options below
A. The EC2 instance running your WAF software is placed between your private subnets and any NATed connections to the internet.
B. The EC2 instance running your WAF software is placed between your public subnets and your Internet Gateway.
C. The EC2 instance running your WAF software is placed between your public subnets and your private subnets.
D. The EC2 instance running your WAF software is included in an Auto Scaling group and placed in between two Elastic load balancers.
Correct Answer: D
The below diagram shows how a WAF sandwich is created. Its the concept of placing the Ec2 instance which hosts the WAF software in between 2 elastic load balancers.
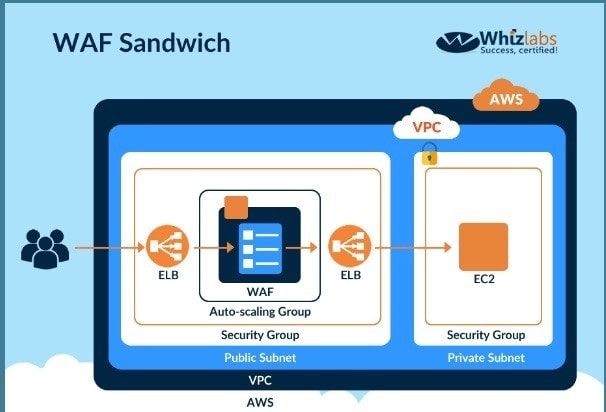
Option A.B and C are incorrect since the EC2 Instance with the WAF software needs to be placed in an Autoscaling Group For more information on a WAF sandwich please refer to the below Link: https://www.cloudaxis.eom/2016/11/2l/waf-sandwich/ The correct answer is: The EC2 instance running your WAF software is included in an Auto Scaling group and placed in between two Elastic load balancers. Submit your Feedback/Queries to our Experts
New Question 5:
Your company is planning on using IAM EC2 and ELB for deployment for their web applications. The security policy mandates that all traffic should be encrypted. Which of the following options will ensure that this requirement is met? Choose 2 answers from the options below.
A. Ensure the load balancer listens on port 80
B. Ensure the load balancer listens on port 443
C. Ensure the HTTPS listener sends requests to the instances on port 443
D. Ensure the HTTPS listener sends requests to the instances on port 80
Correct Answer: BC
The IAM Documentation mentions the following You can create a load balancer that listens on both the HTTP (80) and HTTPS (443) ports. If you specify that the HTTPS listener sends requests to the instances on port 80, the load balancer terminates the requests and communication from the load balancer to the instances is not encrypted, if the HTTPS listener sends requests to the instances on port 443, communication from the load balancer to the instances is encrypted. Option A is invalid because there is a need for secure traffic, so port 80 should not be used Option D is invalid because for the HTTPS listener you need to use port 443 For more information on HTTPS with ELB, please refer to the below Link: https://docs.IAM.amazon.com/elasticloadbalancing/latest/classic/elb-create-https-ssl-load-balancer.html The correct answers are: Ensure the load balancer listens on port 443, Ensure the HTTPS listener sends requests to the instances on port 443 Submit your Feedback/Queries to our Experts
New Question 6:
You have an S3 bucket hosted in IAM. This is used to host promotional videos uploaded by yourself. You need to provide access to users for a limited duration of time. How can this be achieved?
A. Use versioning and enable a timestamp for each version
B. Use Pre-signed URL\’s
C. Use IAM Roles with a timestamp to limit the access
D. Use IAM policies with a timestamp to limit the access
Correct Answer: B
The IAM Documentation mentions the following All objects by default are private. Only the object owner has permission to access these objects. However, the object owner can optionally share objects with others by creating a pre-signed URL using their own security credentials, to grant time-limited permission to download the objects. Option A is invalid because this can be used to prevent accidental deletion of objects Option C is invalid because timestamps are not possible for Roles Option D is invalid because policies is not the right way to limit access based on time For more information on pre-signed URL\’s, please visit the URL: https://docs.IAM.ama2on.com/AmazonS3/latest/dev/ShareObiectPreSisnedURL.html The correct answer is: Use Pre-signed URL\’s Submit your Feedback/Queries to our Experts
New Question 7:
A company is using Amazon Elastic Container Service (Amazon ECS) to deploy an application that deals with sensitive data During a recent security audit, the company identified a security issue in which Amazon RDS credentials were stored with the application code In the company\’s source code repository
A security engineer needs to develop a solution to ensure that database credentials are stored securely and rotated periodically. The credentials should be accessible to the application only The engineer also needs to prevent database administrators from sharing database credentials as plaintext with other teammates. The solution must also minimize administrate overhead
Which solution meets these requirements?
A. Use the IAM Systems Manager Parameter Store to generate database credentials. Use an IAM profile for ECS tasks to restrict access to database credentials to specific containers only.
B. Use IAM Secrets Manager to store database credentials. Use an IAM inline policy for ECS tasks to restrict access to database credentials to specific containers only.
C. Use the IAM Systems Manager Parameter Store to store database credentials. Use IAM roles for ECS tasks to restrict access to database credentials lo specific containers only
D. Use IAM Secrets Manager to store database credentials. Use IAM roles for ECS tasks to restrict access to database credentials to specific containers only.
Correct Answer: D
New Question 8:
A company has public certificates that are managed by AWS Certificate Manager (ACM). The certificates are either imported certificates or managed certificates from ACM with mixed validation methods. A security engineer needs to design a monitoring solution to provide alerts by email when a certificate is approaching its expiration date. What is the MOST operationally efficient way to meet this requirement?
A. Create an AWS Lambda function to list all certificates and to go through each certificate to describe the certificate by using the AWS SDK. Filter on the NotAfter attribute and send an email notification. Use an Amazon EventBridge rate expression to schedule the Lambda function to run daily.
B. Create an Amazon CloudWatch alarm Add all the certificate ARNs in the AWS/CertificateManager namespace to the DaysToExpiry metnc. Configure the alarm to publish a notification to an Amazon Simple Notification Service (Amazon SNS) topic when the value for the DaysToExpiry metric is less than or equal to 31.
C. Set up AWS Security Hub. Turn on the AWS Foundational Security Best Practices standard with integrated ACM to send findings. Configure and use a custom action by creating a rule to match the pattern from the ACM findings on the NotBefore attribute as the event source Create an Amazon Simple Notification Service (Amazon SNS) topic as the target
D. Create an Amazon EventBridge rule by using a predefined pattern for ACM Choose the metric in the ACM Certificate Approaching Expiration event as the event pattern. Create an Amazon Simple Notification Service (Amazon SNS) topic as the target
Correct Answer: D
Using Amazon EventBridge to create a rule for ACM Certificate Approaching Expiration events and configuring an SNS topic as the target provides an operationally efficient way to monitor and alert on certificate expirations. This method leverages AWS\’s native capabilities for event monitoring and notifications, reducing the need for custom implementations and ensuring timely alerts.
New Question 9:
A company has contracted with a third party to audit several IAM accounts. To enable the audit, cross-account IAM roles have been created in each account targeted for audit. The Auditor is having trouble accessing some of the accounts. Which of the following may be causing this problem? (Choose three.)
A. The external ID used by the Auditor is missing or incorrect.
B. The Auditor is using the incorrect password.
C. The Auditor has not been granted sts:AssumeRole for the role in the destination account.
D. The Amazon EC2 role used by the Auditor must be set to the destination account role.
E. The secret key used by the Auditor is missing or incorrect.
F. The role ARN used by the Auditor is missing or incorrect.
Correct Answer: ACF
Using IAM to grant access to a Third-Party Account 1) Create a role to provide access to the require resources 1.1) Create a role policy that specifies the IAM Account ID to be accessed, “sts:AssumeRole” as action, and “sts:ExternalID” as condition 1.2) Create a role using the role policy just created 1.3) Assign a resouce policy to the role. This will provide permission to access resource ARNs to the auditor 2) Repeat steps 1 and 2 on all IAM accounts 3) The auditor connects to the IAM account IAM Security Token Service (STS). The auditor must provide its ExternalID from step 1.2, the ARN of the role he is trying to assume from step 1.3, sts:ExternalID 4) STS provide the auditor with temporary credentials that provides the role access from step 1 https://docs.IAM.amazon.com/IAM/latest/UserGuide/id_roles_create_for- user_externalid.html https://IAM.amazon.com/blogs/security/how-to-audit-cross-account-roles-using-IAM-cloudtrail-and-amazon-cloudwatch-events/
New Question 10:
A company requires that IP packet data be inspected for invalid or malicious content.
Which of the following approaches achieve this requirement? (Choose two.)
A. Configure a proxy solution on Amazon EC2 and route all outbound VPC traffic through it. Perform inspection within proxy software on the EC2 instance.
B. Configure the host-based agent on each EC2 instance within the VPC. Perform inspection within the host-based agent.
C. Enable VPC Flow Logs for all subnets in the VPC. Perform inspection from the Flow Log data within Amazon CloudWatch Logs.
D. Configure Elastic Load Balancing (ELB) access logs. Perform inspection from the log data within the ELB access log files.
E. Configure the CloudWatch Logs agent on each EC2 instance within the VPC. Perform inspection from the log data within CloudWatch Logs.
Correct Answer: AB
“EC2 Instance IDS/IPS solutions offer key features to help protect your EC2 instances. This includes alerting administrators of malicious activity and policy violations, as well as identifying and taking action against attacks. You can use IAM services and third party IDS/IPS solutions offered in IAM Marketplace to stay one step ahead of potential attackers.”
New Question 11:
A security engineer needs to build a solution to turn AWS CloudTrail back on in multiple AWS Regions in case it is ever turned off.
What is the MOST efficient way to implement this solution?
A. Use AWS Config with a managed rule to initiate the AWS-EnableCloudTrail remediation.
B. Create an Amazon EventBridge event with a cloudtrail.amazonaws.com event source and a StartLogging event name to invoke an AWS Lambda function to call the StartLogging API.
C. Create an Amazon CloudWatch alarm with a cloudtrail.amazonaws.com event source and a StopLoggmg event name to invoke an AWS Lambda function to call the StartLogging API.
D. Monitor AWS Trusted Advisor to ensure CloudTrail logging is enabled.
Correct Answer: A
New Question 12:
A company has an organization in AWS Organizations that includes dedicated accounts for each of its business units. The company is collecting all AWS CloudTrail logs from the accounts in a single Amazon S3 bucket in the top-level account. The company\’s IT governance team has access to the top-level account. A security engineer needs to allow each business unit to access its own CloudTrail logs.
The security engineer creates an IAM role in the top-level account for each of the other accounts. For each role the security engineer creates an IAM policy to allow read-only permissions to objects in the S3 bucket with the prefix of the respective logs.
Which action must the security engineer take in each business unit account to allow an IAM user in that account to read the logs?
A. Attach a policy to the IAM user to allow the user to assume the role that was created in the top-level account. Specify the role\’s ARN in the policy.
B. Create an SCP that grants permissions to the top-level account.
C. Use the root account of the business unit account to assume the role that was created in the top-level account. Specify the role\’s ARN in the policy.
D. Forward the credentials of the IAM role in the top-level account to the IAM user in the business unit account.
Correct Answer: A
To allow an IAM user in one AWS account to access resources in another AWS account using IAM roles, the following steps are required:
Create a role in the AWS account that contains the resources (the trusting account) and specify the AWS account that contains the IAM user (the trusted account) as a trusted entity in the role\’s trust policy. This allows users from the trusted
account to assume the role and access resources in the trusting account. Attach a policy to the IAM user in the trusted account that allows the user to assume the role in the trusting account. The policy must specify the ARN of the role that
was created in the trusting account.
The IAM user can then switch roles or use temporary credentials to access the resources in the trusting account.
Verified References:
https://repost.aws/knowledge-center/cross-account-access-iam https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_accou nts_access.html https://docs.aws.amazon.com/IAM/latest/UserGuide/tutorial_cross-accountwith-roles.html
New Question 13:
You are trying to use the Systems Manager to patch a set of EC2 systems. Some of the systems are not getting covered in the patching process. Which of the following can be used to troubleshoot the issue? Choose 3 answers from the options given below.
A. Check to see if the right role has been assigned to the EC2 instances
B. Check to see if the IAM user has the right permissions for EC2
C. Ensure that agent is running on the instances.
D. Check the Instance status by using the Health API.
Correct Answer: ACD
For ensuring that the instances are configured properly you need to ensure the followi . 1) You installed the latest version of the SSM Agent on your instance 2) Your instance is configured with an IAM Identity and Access Management (IAM) role that enables the instance to communicate with the Systems Manager API 3) You can use the Amazon EC2 Health API to quickly determine the following information about Amazon EC2 instances The status of one or more instances The last time the instance sent a heartbeat value The version of the SSM Agent The operating system The version of the EC2Config service (Windows) The status of the EC2Config service (Windows) Option B is invalid because IAM users are not supposed to be directly granted permissions to EC2 Instances For more information on troubleshooting IAM SSM, please visit the following URL: https://docs.IAM.amazon.com/systems-manager/latest/userguide/troubleshooting-remote-commands.html The correct answers are: Check to see if the right role has been assigned to the EC2 Instances, Ensure that agent is running on the Instances., Check the Instance status by using the Health API. Submit your Feedback/Queries to our Experts
New Question 14:
A Devops team is currently looking at the security aspect of their CI/CD pipeline. They are making use of IAM resource? for their infrastructure. They want to ensure that the EC2 Instances don\’t have any high security vulnerabilities. They want to ensure a complete DevSecOps process. How can this be achieved?
A. Use IAM Config to check the state of the EC2 instance for any sort of security issues.
B. Use IAM Inspector API\’s in the pipeline for the EC2 Instances
C. Use IAM Trusted Advisor API\’s in the pipeline for the EC2 Instances
D. Use IAM Security Groups to ensure no vulnerabilities are present
Correct Answer: B
Amazon Inspector offers a programmatic way to find security defects or misconfigurations in your operating systems and applications. Because you can use API calls to access both the processing of assessments and the results of your assessments, integration of the findings into workflow and notification systems is simple. DevOps teams can integrate Amazon Inspector into their CI/CD pipelines and use it to identify any pre- existing issues or when new issues are introduced. Option A.C and D are all incorrect since these services cannot check for Security Vulnerabilities. These can only be checked by the IAM Inspector service. For more information on IAM Security best practices, please refer to below URL: https://d1.IAMstatic.com/whitepapers/Security/IAM Security Best Practices.pdl The correct answer is: Use IAM Inspector API\’s in the pipeline for the EC2 Instances Submit your Feedback/Queries to our Experts
New Question 15:
A company is hosting sensitive data in an IAM S3 bucket. It needs to be ensured that the bucket always remains private. How can this be ensured continually? Choose 2 answers from the options given below A. Use IAM Config to monitor changes to the IAM Bucket
B. Use IAM Lambda function to change the bucket policy
C. Use IAM Trusted Advisor API to monitor the changes to the IAM Bucket
D. Use IAM Lambda function to change the bucket ACL
Correct Answer: AD
One of the IAM Blogs mentions the usage of IAM Config and Lambda to achieve this. Below is the diagram representation of this
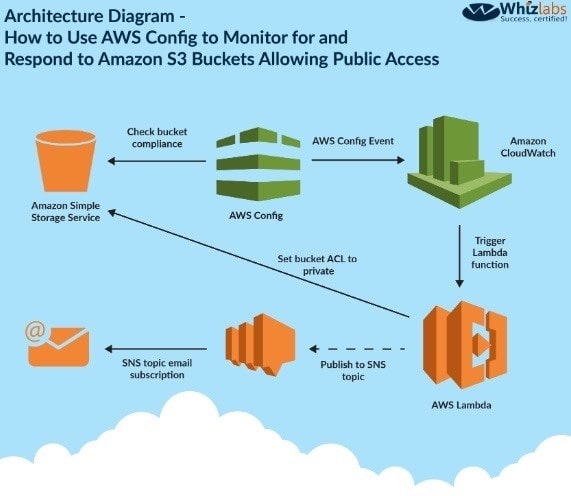
ption C is invalid because the Trusted Advisor API cannot be used to monitor changes to the IAM Bucket Option B doesn\’t seems to be the most appropriate.
1. If the object is in a bucket in which all the objects need to be private and the object is not private anymore, the Lambda function makes a PutObjectAcI call to S3 to make the object private. https://IAM.amazon.com/blogs/security/how-todetect-and-automatically-remediate-unintended-permissions-in-amazon-s3-bbiect-acls-with-cloudwatch-events/
The following link also specifies that Create a new Lambda function to examine an Amazon S3 buckets ACL and bucket policy. If the bucket ACL is found to al public access, the Lambda function overwrites it to be private. If a bucket policy is found, the Lambda function creatt an SNS message, puts the policy in the message body, and publishes it to the Amazon SNS topic we created. Bucket policies can be complex, and overwriting your policy may cause unexpected loss of access, so this Lambda function doesn\’t attempt to alter your policy in any way. https://IAM.amazon.com/blogs/security/how-to-useIAM-config-to-monitor-for-and-respond-to-amazon-s3-buckets-allowinj
Based on these facts Option D seems to be more appropriate then Option B. For more information on implementation of this use case, please refer to the Link: https://IAM.amazon.com/blogs/security/how-to-use-IAM-config-to-monitor-for-and-respond-to-amazon-s3-buckets-allowinj
The correct answers are: Use IAM Config to monitor changes to the IAM Bucket Use IAM Lambda function to change the bucket ACL
…
Leads4Pass SCS-C02 dumps 2025 provide complete exam preparation materials including 816 New dumps exam questions and answers, guaranteed to be practical and useful, as well as PDF and VCE exam practice tools to help you easily prepare for the AWS Certified Security – Specialty (scs-c02) exam!
SCS-C02 Exam Key Frequently Asked Questions
What certifications are required before taking the SCS-C02 exam?
You do not need to obtain any specific certification before preparing for this certification. However, candidates typically earn the AWS Certified Solutions Architect – Associate and/or AWS Certified Solutions Architect – Professional level before taking the AWS Certified Security – Professional exam.
SCS-C02 VS SCS-C01
The latest AWS Certified Security Specialty SCS-C02 exam has some similarities with its previous version, but it also introduces a plethora of new knowledge areas, services, domains, and features. One notable change is the brand new “Management & Security Governance” domain. This new addition checks your know-how in developing a strategy to centrally deploy and manage AWS accounts, implementing a secure and consistent deployment strategy for cloud resources, and evaluating the compliance of AWS resources, among others.
How will AWS Certified Security – Specialty help my career development?
AWS Certified Security – Specialty certification will expand your career scope, build your credibility, and establish a trustworthy connection with your collaborators. Holding this certification can meet the requirements of those with relevant needs! What’s more important is to increase your career options and make your career plans richer!